
Domains 101: Everything To Know About Registering A New Domain
Every minute, more than 70 new domain names are registered on the internet. In addition, 571 new websites are created every minute. Currently, there are close to a billion domains, however, it has been estimated that up to 70% of these domains are parked and not in use. No matter, even with at least 280 million active domains, there is still a lot of competition for views and clicks. If you want to have your own website, careful planning is required

Most Common Spectrum Analyzer Types Used For Electronics
If you have just started a career in the electronics industry, you have probably heard about spectrum analyzers. These devices are used to analyze the frequency spectrum of radio signals, also known as radio frequency, or RF. However, there are several types of spectrum analyzers that can do this job in a variety of ways, just like fitness technology. Find out about the different kinds of spectrum analyzers below. Parallel-Filter Spectrum Analyzers Parallel-filter analyzers are a type of real-time spectrum analyzers.

5 Important Linux vs Windows Hosting Differences For Web Development
Web developers have to make an informed decision when it comes to picking a hosting solution when they want to start a blog or build some other type of website. That is why it is so important to understand the differences between Linux vs Windows hosting accounts. Keep reading below to learn the differences between Linux hosting and Windows hosting. This way, you can make the best choice to simplify the process of building and managing a website. Customization Typically, Linux

4 Steps You Can Take Today To Improve Your Software Platforms
Computer security is critical to the success of your business. A 2014 study suggested that 43 percent of companies suffered a data breach in a calendar year. You don’t want to add your business to the list. Here are four steps you can take today to improve your software platforms. Control Access Do all of your workers enjoy the same data access? They shouldn’t. Most companies have realized that data breaches often occur at the lowest levels. A worker with too

Benefits Of A Static IP Buy On Streamlined Business Operations
Business owners of all technical abilities can benefit from paying for a static IP address. But, how are you supposed to know this if you hardly know the difference between a static IP address and a dynamic IP address? You may not want to be parted from your hard earned money for something that you have no understanding of. Here are the five reasons why a static IP buy will provide a great return on investment for many years to come.

Essential Network Troubleshooting Tools For All System Admins
Systems administrators like yourself are required to complete a whole laundry list of different tasks. Network troubleshooting is perhaps one of the most frustrating responsibilities of the position. Thankfully, there is network troubleshooting software that can help simplify the task. Here are the top network troubleshooting tools that every sysadmin should have in their arsenal. Iperf Iperf is one of the network diagnostics tools used by all the pros. You can use the software to measure throughput, packet loss and jitter.

Bad App Design vs Good App Design: What to Avoid & What to Aim For
Apps are the most popular form of mobile phone engagement. The average person spends around 3.5 hours a day browsing apps, and 85% of mobile phone users report a preference to apps over mobile websites. The popularity of the platform comes from its dynamic user experience. Consumers report ease of use, convenience and accessibility as the primary drivers behind their attraction to apps over mobile websites. To meet user expectations, though, developers must ensure they follow practices of good app design.

Top QA Testing Tools To Automate Time Consuming Processes
If you are a test management professional responsible for ensuring the quality of various software, it can be a stressful job. Making sure that each and every detail works together perfectly is quite the task. However, there are solutions that can help make this task a bit simpler. Here are the top five QA testing software solutions that can streamline this time consuming task. qTest qTest is one of the best test management tools for Agile testing and quality assurance teams.

How Insurance IoT Gadgets Are Revolutionizing The Industry
The Internet of Things is revolutionizing technology as we know it. The insurance industry, however, was not one of the sectors anyone would have expected this technology to take off. But, it is. IoT technology applications within the insurance industry are just starting to gain momentum. Here are the five ways insurance IoT applications are revolutionizing the industry unexpectedly that all techies are sure to want to know. Snapshot Progressive Snapshot is perhaps the most well-recognized IoT application within the insurance

Stop Waiting And Go To IPv6 For Upgraded Security
Internet Protocol (IP) is an addressing system used to identify different devices on a network. Data packets are sent from a host to a destination based on IP addresses. IP is the primary foundation for how we share information on the Internet. The most recent version of the Internet Protocol is version 6 (IPv6). This blog post will detail the distinctions between version 4 and 6 as well as clue you into the benefits of adopting the IPv6 standard. How Is

Top Hosting Software For A Customizable Control Panel Solution
If you want to create your own website, you have to figure out how you will manage your hosting servers after you learn PHP for beginners. There are many hosting software solutions out there for you to consider. Keep reading below to learn the top hosting control panel software available for new web developers like yourself. Webmin Webmin is one of the most popular web hosting control panels out today. This software is a web-based system configuration tool for Unix systems
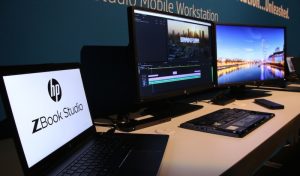
Top 5 Workstation Computers For Maximum Computing Power At Home
Freelancers do not have the benefit of being supplied a workstation by their employer. However, this can be an advantage. It allows you to select the perfect workstation computer for your particular needs and preferences. It will cost you quite a bit of money, but it is a necessary investment for your career. Keep reading below to learn the top workstation computers available for you to consider using in your home office, shared working space or wherever. Dell Precision Tower 5810

How To Make New Friends Using Technology Wisely
Adults are busy between work, bills and family. It might seem tough to make new friends. Whether you are in your 20’s, 30’s or older, you can use technology to help find and meet new people. Of course, the way people meet, interact and socialize have changed. Rather than fear the change, use technology to your advantage. Here are some of the best ways to make new friends by using technology. Get Your Social Media Set Up With over a billion

Unknown Citizen Journalists That Revolutionized News Media Reporting
Citizen journalism occurs when the public plays an active role in the gathering and reporting news. This could be anything from recording video on an iPhone to sending out a

How Modern Cancer Research Findings May Lead To A Cure For Cancer
New technologies are developing daily, each designed with a specific purpose and audience. In medical research, advancing technologies have been designed to detect cancer cells in blood. In this post,

Best Apps For Pharmacists To Have Concise Database At Your Fingertips
Pharmacy companies are constantly coming out with new, innovative ways to provide healthcare to the community. As technology continues to expand, more and more opportunities are coming to the app

7 Reformatting Computer Preparation Steps To Take To Protect Data
Reformatting is the process of completely erasing everything from the hard drive of your computer and then reinstalling the essentials – like your operating system, applications, and personal files. It’s

Straight Talk Walmart Phones Make Unlimited Data Affordable
Walmart is known for selling a variety of products at the lowest price. Their phones and electronics are no exception. Walmart phones offer a wide selection from disposable phones for

How To Access Google Timeline To Edit Saved Location Tracking Entries
Last year, Google Maps introduced a timeline map. This feature allows users to revisit their travels from any given day. In this post, Internet users can learn five exciting features

Prime95 Download Sources To Test Overclocked CPU Stability For Free
Prime95 is software designed to stress test personal computers to ensure stability. The free software was designed by George Woltman to find new mersenne prime numbers. It is frequently used

Most Exciting Google X Moonshot Factory Innovations Not Yet Released
Google X, now referred to as X, is Google’s semi-secret facility in California. The research and development company aims to, according to the website, “invent and launch ‘moonshot’ technologies that

Best Mini Camera Choices For WiFi Connected HDR Surveillance Images
A smartphone may not always be the best option for recording video, depending on the situation. When it comes to Facebook rules, you can post almost anything shot on your

New Abbey Roads Studio Audio Technology Offers Mastering Services
Arguably the most famous recording studio in the world, it is difficult not to think about The Beatles when mentioning Abbeys Road Studios in London, U.K. Some of the world’s

How Google Mail Account Domains Differ In Countries Around The Globe
Gmail users in the United States know it is Google’s email service, but hardly anyone refers to it as Google Mail. This opposite may be the case if you reside

Important Protections Antispyware Solutions Offer PC Users
SUPERAntiSpyware is a free software that offers a range of protection to computer users from viruses, adware, worms and spyware (among others). Still, most average computer users don’t think of

How Backdoors Offer Perfect Hacking Strategies For Encrypted Devices
Backdoors are methods by which a technology user can gain unauthorized access to a program or computer function outside of normal security parameters and proper IPtables confirguation. While the average
